Impersonating Your Brand
Anytime anybody impersonates you, it's a great compliment. – Robert Wagner
In my role at Flipboard a similar position. I'll start with something that is a bit off topic from the typical spammers that we uncovered just the other day: someone impersonating our brand .... because I am actually not 100% sure how we should fully handle it, and would love your thoughts.
The Scam
We received a report over our standard help channels from a non-user that they were cold called by a twitter (a.k.a. X) user claiming to work for Flipboard. They were made some vague promises if they signed up and after saying no ... well .... let's just say this scammer cussed them out with some not so nice language.
After working with the user (and promising them this was not us) we uncovered this account on X which was doing the impersonation.
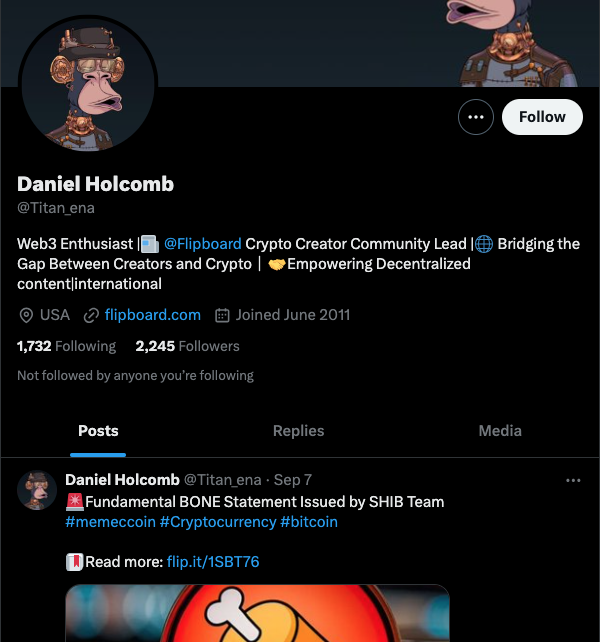
The Research
Nothing on that account there is legit. Notice the flip[.].it url that redirects to some sort of statement on the SHIB token, which seems part of their scam. Well, when a Flipboard user creates a short url, we keep track of the account that created it. In this case, a simple lookup uncovered the account used to create the link. Luckily, they had accessed that account the day we were notified of this. We keep logs for around 14-21 days from key systems in order to help debug problems legit users report. In this case, I was able to find a log in our haproxy routers for this account:
./12/haproxy-standard:2024-09-25T12:40:09+00:00 [X.X.X.X] <user.notice> haproxystandard[3707085]: Y.Y.Y.Y:2600 [25/Sep/2024:12:40:09.912] fe-production-https be-production-fly-standard/0443f7ece3c501810 0/0/1/0/1 304 168 - - ---- 546/305/0/0/0 0/0 {fbprod.flipboard.com|49.130.131.81, 64.252.103.219|Amazon CloudFront|} "GET /v1/static/config.json?userid=YYYY&ver=4.3.29&device=iphone-17.4.1&model=iPhone11%2C6&lang=zh-Hant-HK HTTP/1.1"
This is a request from their device looking for initial configuration information. There are a few things to notice here: – the ip address they request originated from is 49.130.131.81 – their language is set to traditional chinese, Hong Kong – they are using an iphone and a fairly recent version of our software
NOTE: we utilize this information to ensure the user experience works for the device, language and location of the user and the details above were sanitized
Doing a whois lookup on that ip address and we get confirmation this user is coming from Hong Kong

Great, so now what? I wanted to see if there might be more than 1 user or account on X executing this scam. So, I looked at their 2,245 followers (X only let me search some of them) and quickly found 2 other accounts done in similar fashion: LoisFlipboard and DaisyFlipboard. Continuing down this path, you find more and more .....
Next, I wanted to see if each of these accounts were separate users or the same, so I looked for additionally references flip[.]it links and sure enough, they all tracked back to the same Flipboard account.
The Actions
So, the next question is, what should we do about this? It clearly hurts our brand to have someone scamming people in our name, but also, in general, this is just a bad person doing evil things for self gain. We cannot block all the ip addresses they use .... legitimate users use them. We obviously suspended the account, but they can always easily create a new account on Flipboard. We do have a way to block a device from accessing our service, but I won't go into those details. However, this scam is being executed from X itself, not Flipboard.
X does offer a “report this user” and we could do that for each of these accounts for impersonating out brand and keep trying to hunt them all down. But check this out .... they want you to fill out a form when you get to this part:
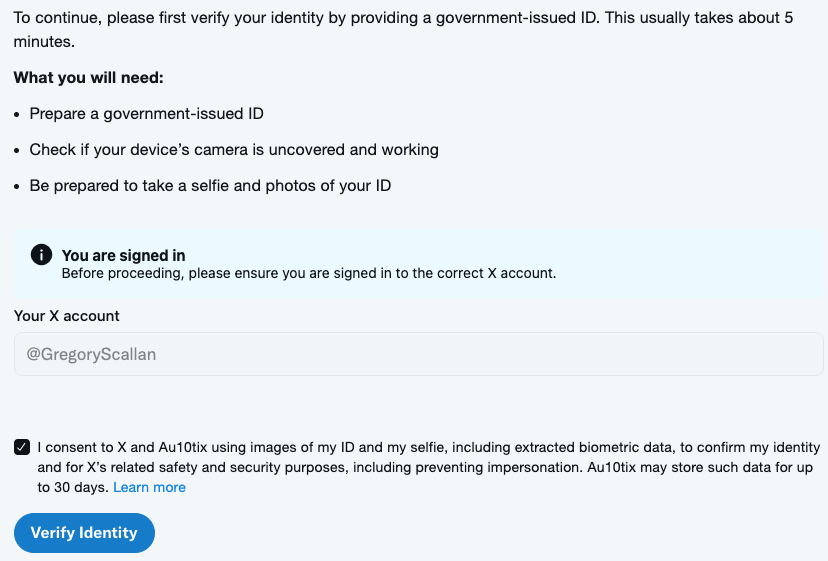
Would you send up images of government issued id's and consent to X's trust and safety team to extract biometric data? Especially after they dissolved their Trust and Safety Council?
We do have a plan, but I am curious ... would you send up personal information like this to X and trust how it is being handled? Would you try and track down all the accounts on X taking these nefarious actions and, if so, how? Would you just ignore it? What would you do next?